Product of the Week: IAR Embedded Workbench
March 01, 2021
Blog
Most embedded designs have a similar starting point – sitting down to write code. Obviously, we’re not writing line by line like the old days, and the reason for that is development tools have done such a good job at automating that process.
One such tool is IAR Systems’ Embedded Workbench, already in use by more than 150,000 embedded developers worldwide. Recent updates have kept the integrated development environment (IDE) and its C/C++ compiler, debug, and trace functionality at the forefront of technology. Meanwhile, the integratable C-STAT and C-RUN code analysis tools and C-Trust and Embedded Trust functional safety and security add-ons make the tool suite well-equipped for anything modern applications can throw its way.
Among build enhancements, additional device support, and other upgrades, the latest version of IAR Embedded Workbench, version 9.10 now supports 64-bit Arm cores through extensions for the Armv8-A execution model AArch64 and the Arm AArch-64 data models ILP32 and LP64. The tool now also includes compatibility with the Arm AEABI 64-bit, C++ IA64 ABI, and C++ IA64 exceptions ABI, which allows it to be used for single- or multicore development with cores that include the Arm Cortex-A35, Cortex-A53, and Cortex-A55.
This adds to support for 14,000 devices and 30 different processor families based on the Arm, RISC-V, AVR, and other microarchitectures, such as NXP's i.MX line, STM8, MSP430, and more.
In terms of functional safety, Embedded Workbench provides coverage for standards such as IEC 61508, ISO 26262, EN 50128, EN 50657, IEC 62403, ISO 25119, IEC 62061, ISO 13849-1, IEC 61511-1, IEC 60730-1, and others.
IAR Embedded Workbench in Action
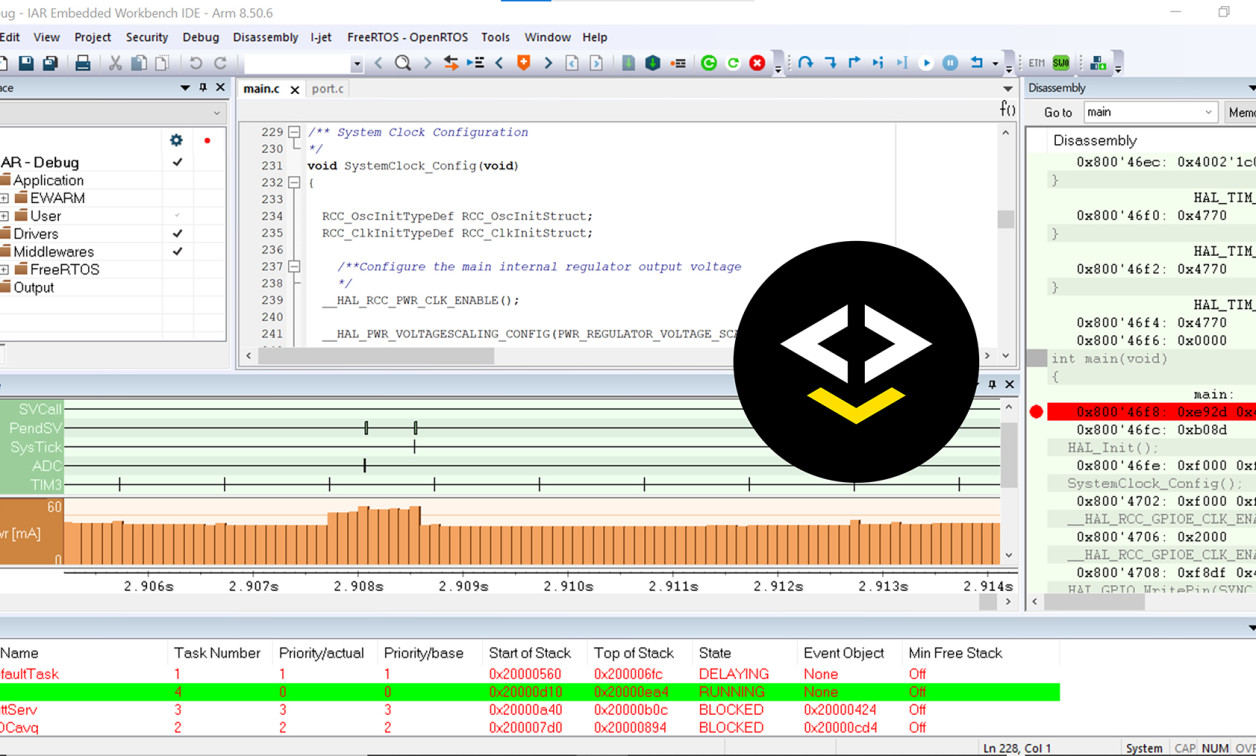
The heart of the Embedded Workbench is he C/C++ compiler, which is the fastest compiler on the market in terms of speed of execution and also generates the most tightest, most efficient code per the CoreMark standard benchmark.
Call stack information generated by the compiler provides a view of the complete stack without runtime penalty by selecting any function in the call stack with information on local variables and available registers. The compiler is comprised of a macro system that allows the user to automate the debugging process and simulate peripheral devices. While the system is running, the tool is able to interrupt, if needed, to perform tasks such as reading and writing memory or files, resets, string operations, and JTAG commands. The compiler offers different dialects of the C/C++ programming language, as well as specific extensions for embedded programming.
The C-SPY debugging tool is designed to be used in conjunction with the IAR C/C++ compiler within the tool suite’s IDE. As a high-level language debugger, C-SPY offers source- and assembly-level debugging, allowing the user to switch between the two. Single-stepping at the function call level allows inside expressions and function calls to be single stepped. Additionally, the function identifies every statement and call as a step point. Code and data breakpoints allow the user to set custom breakpoints depending on the application being debugged. Monitoring variables and expressions is included, as well as container awareness for an overview of STL lists, vectors, and other debugging opportunities.
The C-STAT static analysis tool provides the user with potential code errors by performing analysis at the source code level. Following industry coding standards, the tool complies with MISRA C:2012, MISRA C++:2008, and MISRA C:2004, as well as potential issues covered by CWE. The tool is also aligned with the coding standard CERT C for secure coding.
On the other hand, C-RUN runtime analysis finds errors at runtime while monitoring the application's execution. More specifically, C-RUN also analyzes C/C++ coding, provides call stack information for each error, code correlation and graphical feedback, error filter management, boundary checking of arrays and other objects, buffer overflow detection, checking of value changes, bit losses in shift operations, heap and memory leak checking, and more.
Both C-Trust and Embedded Trust are offered on the tool as a security development environment to allow users to encrypt their codebase. C-Trust is an extension of the IAR workbench that also provides the user with Preconfigured Security Contexts, which allow the user to customize security contexts for the specific needs of their system. For example, organizations can choose from compounded cryptographic device entities and ownership structures, Roots of Trust (RoTs) for device authentication and authorization, Secure Boot Manager extensions, patches and updates, and identity delegation for cloud infrastructure onboarding.
By using these tools to design-in “security from inception,” a lot of the heavy lift security engineering down the road can be alleviated. In addition, the user has the ability to set manufacturing limits to avoid cloned or counterfeit products.
Getting Started with IAR Embedded Workbench
After selecting a processor to work with and tool of choice, the user begins on the IAR Information Center page of that particular device. The information center page features options for getting started, as well as a user guide section providing example projects demonstrating device-dependent hardware peripherals dependent and/or evaluation boards sourced from various semiconductor companies.
Also featured on the information page are options for integrating solutions that range from middleware to RTOS components from IAR partners. More options on the information page include tutorials, support, and release notes. The My Pages section also provides the user with the latest updates for upgrading the tool and license transferring.
For more information on IAR Embedded Workbench, including a free trial of IAR Embedded Workbench for Arm, visit www.iar.com or check out the resources below.
Additional Resources:
-
IAR Embedded Workbench for Arm Product Page: www.iar.com/products/architectures/arm/iar-embedded-workbench-for-arm/
- IAR Embedded Workbench Functional Safety Webpage: www.iar.com/products/requirements/functional-safety/iar-embedded-workbench-for-arm-functional-safety
-
Free Trial of IAR Embedded Workbench for Arm: www.iar.com/products/architectures/arm/iar-embedded-workbench-for-arm/iar-embedded-workbench-for-arm---free-trial-version
- Introduction to C-SPY Debugging for Arm Cores: www.iarsys.co.jp/download/LMS2/arm/8101/ewarm8101doc/arm/doc/EWARM_DebuggingGuide.ENU.pdf
-
C-STAT Product Page: www.iar.com/products/c-stat
-
C-RUN Product Page: www.iar.com/products/c-run
-
C-TRUST Product Page: www.iar.com/products/requirements/security/c-trust
- Embedded Trust Product Page: www.iar.com/products/requirements/security/embedded-trust