Understand the risk associated with the Internet of Things: Why would a hacker attack my toaster?
May 07, 2015

Why would a hacker attack my toaster? This question came up recently from an individual trying to discount security and the Internet of Things (IoT)....
Why would a hacker attack my toaster? This question came up recently from an individual trying to discount security and the Internet of Things (IoT). Is it reasonable to think that a hacker would attack a toaster, or does it verge on the absurd?
The IoT contains security-critical nodes, such as those running power grids, medical devices, and automobiles. Clearly, we should demand that security be considered in these designs. Yet, it also contains consumer electronics that don’t appear to have the same safety and security concerns. Should consumers and manufacturers be concerned about security in these devices as well?
Let’s explore this topic further by exploring the threats presented to a hypothetical Internet-enabled toaster and ask three questions:
- Are toasters and other consumer IoT devices exploitable?
- Why would a hacker attack my toaster?
- Is it a problem if a hacker attacks my toaster?
It’s definitely worth addressing the question of whether toasters and other consumer IoT devices are exploitable. This is certainly the case because current devices have numerous vulnerabilities and frequently remain on the Internet unpatched many years after the vulnerability’s discovery.
Current consumer devices on the IoT have numerous vulnerabilities, validated by a 2014 study by HP’s Fortify Division. The team picked ten of the most popular consumer IoT devices, and found an alarming number of vulnerabilities on each device. In fact, 70 percent of the devices didn’t correctly encrypt communications to the cloud; 60 percent raised security concerns with their web interface; and 60 percent didn’t use any encryption when downloading software updates. This study demonstrates how serious vulnerabilities are on today’s consumer IoT devices.
Second, consumer IoT devices frequently don’t receive critical updates. Devices with known vulnerabilities may continue to be vulnerable on the Internet for 5 to 15 years after the vulnerability is discovered and could be fixed. For example, a recent vulnerability known as Misfortune Cookie allowed an attacker to remotely control an embedded system. The web server vendor introduced the vulnerability in 2002 and fixed it in 2005. A recent Internet scan found that of the 133,660 publicly accessible hosts running the affected web server, more than 50 percent still ran vulnerable copies of the code. Ten years later, these devices remain unpatched and vulnerable on the public Internet!
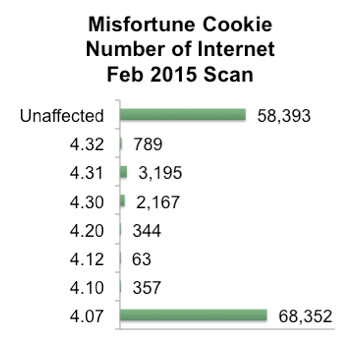
These two reasons cause security expert Bruce Schneier to remark, “We’re at a crisis point now with regard to the security of embedded systems, where computing is embedded into the hardware itself – as with the Internet of Things. These embedded computers are riddled with vulnerabilities, and there’s no good way to patch them.”
Consumer IoT systems today are sadly vulnerable. However, this may be of little concern if consumer IoT systems aren’t an interesting target. So the next question that needs to be asked is “Why would a hacker attack my toaster?”
To explore, we will classify attacks into two categories: targeted and opportunistic. Targeted attacks are those where the attacker targets a person or an organization of high value, such as the recent hack of Sony Pictures. As best as we know, hackers targeted Sony due to the impending release of the movie “The Interview,” which mocked the North Korean government. The hackers had no interest in hacking other studios at the time; they hacked Sony because the particular organization was of high value to the attackers.

Other attacks demonstrate this same theme: Stuxnet was targeted at the Natanz nuclear plant in Iran; it was designed to ignore other industrial control systems. Various celebrities in the United States have had private photos leaked; the same attackers were not interested in leaking photos from random people. In both of these instances, the person or organization was of high value to the attackers. Given this definition, it’s unlikely to see any reason that an attacker would target an individual’s personal toaster, as this would not be of high value to attackers.
Opportunistic attacks
Opportunistic attacks are those that are focused on where the attackers believe they can get the biggest economic gain. The attacks on Target, stealing information from 40 million credit cards, fall into this camp. The attackers likely didn’t care what specific organization they attacked, but rather were looking for economic gains. The economic gains turned out to be substantial, as each credit card sold on the black market for $25 to $40.
Another area of opportunistic attacks is related to malware infected machines used to send spam. These machines are joined together to create networks of infected machines, known as botnets. One botnet, the Srizbi botnet, has about 450,000 infected computers that are believed to send 40 percent to 60 percent of worldwide spam. For every machine, it doesn’t really matter whether the infected computer is running air traffic control at a busy airport, the desktop machine of a wall-street trader, or is used for e-mail by a grandma. The botnet attackers don’t care about the purpose of the machine; it’s simply an infected node on the Internet.

Given this definition, it’s actually plausible that a hacker would infect a toaster. Truthfully, the attacker doesn’t really care that it’s a toaster at all, but rather that it’s a device than can be easily exploited on the Internet and can bring economic gain.
The economics
Since opportunistic attacks are about underlying economics, it’s important to understand whether the economics of the situation justify the attack. How much money could an attacker expect to make through a single infected toaster, and how can an attacker make money from attacking a toaster? There are two obvious ways – obtaining personal information inside the home network, and using the toaster to send spam and conduct denial-of-service attacks.
First, there’s value by obtaining personal information inside the home network. However, personal information is worth far less on the black market than many would think. A social security number is worth only about $5 on the black market. Credit card numbers stored on a computer are worth about the same. The login to a bank account is worth only 2 percent to 4 percent of the balance. And access to a webcam is only worth $1. The price of these things on the black market is quite low.

Second, there’s value by the attacker remotely controlling the toaster along with a network of infected machines to send SPAM and conduct denial-of-service attacks. Such a network is known as a botnet. Renting a botnet on one black market site costs $200 per day for 1,000 infected hosts. This means that a single toaster would be worth 20 cents a day or $6 a month. Assuming the toaster would be infected on average for six months, the total value would be about $36. Again, this value is low.
Combining the ability for an attacker to monetize personal information and the toaster running as a botnet, a reasonable estimate is that the toaster is worth $50 for an attacker. This is clearly not valuable enough for an attacker to target. The cost of an attacker’s time to design an attack is likely thousands of dollars. Therefore, attacking a single toaster doesn’t make good economic sense for the attacker.
However, if the attacker can attack many Internet-enabled toasters of the same brand, the economics change. If a manufacturer sells 500,000 of a certain model of Internet-enabled toasters, then things become interesting. If the attacker were able to infect 5 percent of them, there is now $1.25M to be gained. If the attacker were able to infect all of them, it would be $25M. An attacker, therefore, has the incentive to attack many toasters and join them together.

In short, hackers have an incentive to create an army of malware-infected toasters. The key to this attack is scale. Just as the Szribi botnet, many infected nodes on the IoT can bring a large amount of value to the attacker.
Since there’s an economic case for a hacker to attack an Internet-enabled toaster, it still can’t be taken for granted that this is an actual problem. Maybe a malware-infected toaster will just be “infected” and nobody will be the wiser. This is one possibility, but there are a number of other options that could also occur, the toaster could:
- Slow your Internet
- Steal your personal information
- Fail to turn on
- Burn your toast
- Be publicly known as “hacked”
- Fail to run safety software and start a fire
For a consumer, these scenarios range from those unlikely to cause the toaster to be blamed (slows your Internet, steals your personal information) to those that are downright scary (publicly known as “hacked” and fails to run safely and starts a fire). These scenarios could be very much a problem.

One scenario deserves special attention: the toaster fails to run safely and starts a fire. A colleague experienced this when his toaster jammed and erupted in flames, scorching the kitchen. This was a mechanical failure, but as toasters are added to the IoT, the heating elements will increasingly be controlled by software. If an attacker infects a toaster, the attacker could even cause a house to burn down. This scenario is scary for both the consumer and the manufacturer.
If we consider the above outcomes for the consumer, we can see two possibilities: nobody notices the device is infected or people notice that the device doesn’t function correctly or is infected and they demand a correction of the problem. In the former situation, the likely outcomes are a slower of your Internet, a theft of your personal information, or nothing. In the latter situation, the outcomes might be, the toaster fails to turn on or off, you’re publicly known as “hacked,” or safety software fails to run and a fire starts.
How expensive could this second scenario be for the manufacturer? There are four likely expenses that might occur: warranty replacements, product recalls, brand tarnishing, and possibly product liability losses. Rough estimates of the costs:
- Warranty replacements – $1.75M, if it costs $70 to replace 5 percent of the toasters.
- Product recalls – $22.5M, if it costs $60 to recall 75 percent of the toasters.
- Brand tarnishing – $12.5M to $40B. If the brand is tarnished, the manufacturer will be forced to discount the price to sell the same quantity. The manufacturer might only need to discount all toasters for the next year ($12.5M) or possibly discount all products ($40B).
- Product liability losses – hard to estimate, but could be extremely costly. This number is especially big if it includes liability related to fires started by infected toasters.
Given these costs and risks, it seems wise for Internet-enabled toaster makers to care about the toaster being hacked. Given the risks, a consumer of Internet-enabled toasters should care as well.
Coming back to our original questions, we must conclude three things: toasters and other consumer IoT devices are certainly exploitable. A hacker does have an incentive to attack many toasters as part of an opportunistic attack. It’s likely a costly problem for both the consumer and the manufacturer if a hacker attacks many toasters from that manufacturer.
Beyond toasters
An Internet-enabled toaster is only one example. It helps illustrate the reasoning behind opportunistic attacks infecting many similar devices, rather than targeted attacks of individual devices. Opportunistic attacks are likely the greater threat for most Things in the IoT today.
We live in the convergence of massive growth in the IoT and a steady increase in cybercrime. Given this convergence and our analysis, it’s important to consider any Thing as a potential target. It’s also important to consider that the device could be exploited simply because it’s connected to the Internet, as enough connected devices bring value to an attacker.
Therefore, it’s critically important to consider and think deeply through security for any device on the Internet of Things. And thus we can prevent the otherwise inevitable, army of malware-infected toasters.




