There's more to securing the IoT than you're aware of
September 15, 2014

Many would argue that the consumer and Industrial internet of Things (IoT) are improving the quality of our lives and the environment by reducing poll...
Many would argue that the consumer and Industrial internet of Things (IoT) are improving the quality of our lives and the environment by reducing pollution and augmenting productivity and efficiency. For instance, think of somebody living in Nice, France (see my blog on smart cities) who has experienced – thanks to the smart parking system – a reduction of more than 30 minutes in the time needed to park downtown. This not only improves this person’s overall experience, it also reduces the CO2 emissions caused by the car being driven around in search of a parking spot. In another example, consider smart refrigerators. These appliances can keep track of the food they hold, warn you about expiration dates, suggest recipes, and help with the shopping list. Who wouldn’t want that? But in this wonderful connected world, all that glitters is not gold.
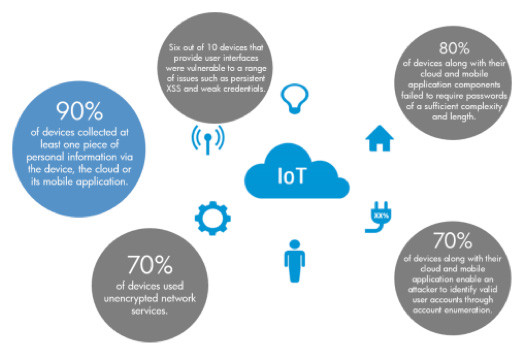
Several industry reports have highlighted a series of security holes. The recent HP Fortify study on IoT security notes that 70 percent of the devices don’t use transport security, thus sending unencrypted information over the Internet! In addition, 90 percent of the devices collected some form of personal information. And a relatively high number of devices use trivial passwords, like 1234. Imagine how this lack of security can turn a digital paradise into hell if somebody, other than you, gained control of your appliances.
Let’s turn our attention from the consumer IoT to the industrial IoT. Here, security is even more important as the devices involved aren’t simple appliances but power grids, aircraft engines, city lightning, sewers, etc. Thus, the impact of a security hole can be far more devastating than that of somebody hacking your refrigerator.
Many IoT security reports argue that a big part of the security issues can be solved by properly applying well-known security principles and techniques, such as using transport encryption, robust passwords, supporting secure firmware and OS upgrades, avoiding cross-scripting attach, etc. Yet most of these reports focus on securing the interaction between a device and a cloud and don’t address the problem of data security in general.
If we consider a more sophisticated IoT application, such as smart cities or smart grids, we quickly realize that access to information needs to be properly regulated. For instance, it may be acceptable to allow everyone to learn about the level of production of a given electric power generator. On the other hand, it’s necessary to allow only specific users access to set the production target. Likewise, for privacy reasons, you may be happy that the position of your car is known when it gets stolen.
Clearly, both the consumer and industrial IoTs need more than the ability to secure access and pipes through which the data flows. It’s essential for these systems to properly address data security. Yet, today few IoT applications are providing support for data security in the form of controlled access. The main reason being the lack of support from the infrastructure they rely on.
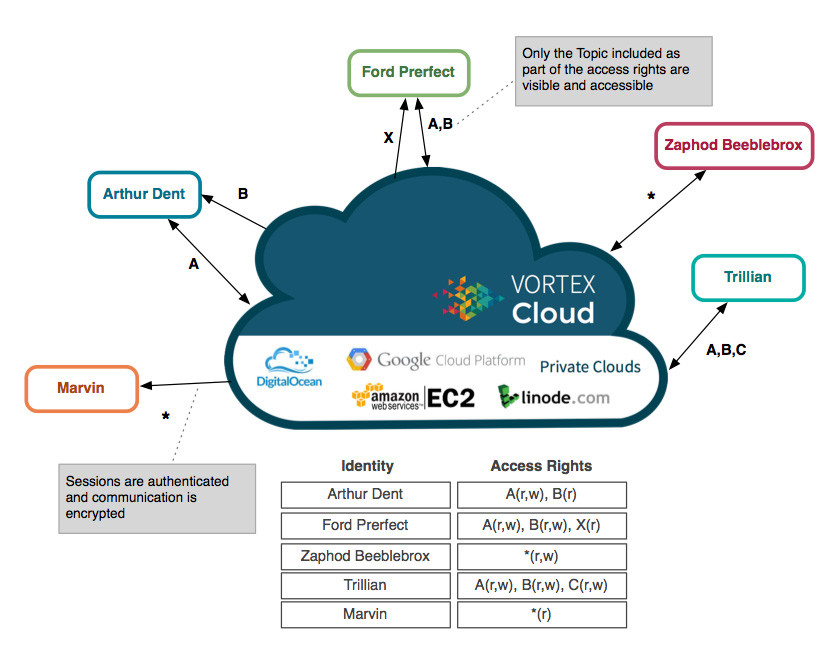
IoT systems interested in having a full security solution, including access control on data flows, should look at platforms based on data distribution service (DDS). DDS has recently been equipped with a security standard that, along with introducing transport security, allows to control access to data. PrismTech’s DDS-based Vortex, for instance, supports authentication and transport security as well as Topic-based access control to handle allowed operations. This includes create, read, update, and delete operations that an application can perform on a given kind of information.
The figure shows a hypothetical system in which different users are allowed different access rights on the various kinds of information. Arthur Dent can read and write the topic A and only read the topic B, while Zaphod Beeblebrox can read and write any kind of information. Poor Marvin can read everything and write nothing.
Clearly, security can’t be an afterthought in IoT applications as the implications can be severe. Furthermore, IoT applications have to think beyond basic transport security and start to reason about data access control. The OMG DDS as a data sharing standard provides a suitable infrastructure for tackling all distribution and security aspects required by IoT applications.
Angelo Corsaro, Ph.D., is the Chief Technology Officer at PrismTech. He directs the company’s technology strategy, planning, evolution, and evangelism. He also leads the strategic standardization at the Object Management Group, where he co-chairs the DDS Special Interest Group and serves on its Architecture Board. Angelo earned a Ph.D. and a M.S. in Computer Science from the Washington University in St. Louis, and a Laurea Magna cum Laude in Computer Engineering from the University of Catania, Italy.